Cloud Computing Research Guidance | Thesis list
by blog_admin
Latest cloud computing Research Guidance
A rising strategy nowadays is cloud computing. Latest cloud computing Research Guidance can be done. As of late it is discovered that investigators have interest in utilizing cloud for carrying out technical applications and also the enormous associations are on the edge of changing over to hybrid cloud. Numerous applications which are very complex need parallel processing for executing the jobs efficiently. Because of the synchronization and communication among processes which run parallel, there is a reduction in usage of resources of CPU. It is fundamental for a data center to accomplish the use of hubs while keeping up the level of responsiveness of jobs which are running parallel. The cloud computing is pulling in an expanded number of uses to keep running in the data centers which are remote. Numerous intricate applications necessitate capabilities of parallel processing. A portion of the applications which are running parallel demonstrate a decline in usage of resources of CPU at whatever point there is an expansion in parallelism only when there is no planning of jobs accurately then it lessens the execution of a computer. Cloud computing thesis Consultant can provide guidance in cloud computing various latest current domains.
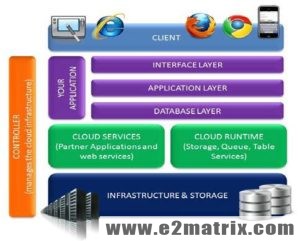
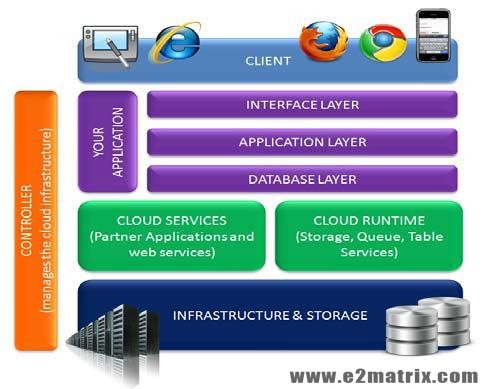
Fig. 1: Layered View of Cloud Architecture
There are three main layers of architecture of cloud computing, for the software which necessitate services over Internet on demand. Figure 2 demonstrates diverse layers of architecture of cloud. Cloud Computing thesis list contain all of this services in their implementation.
- Infrastructure as a Service (IaaS): This IaaS layer conveys components of hardware (such as storage and server) and also software which serve as services.
- Platform as a Service (PaaS): The persons who develop the application of cloud are the main who use this layer. Load balancing, integration with distinctive services (like email services) and automatic scaling are the key advantages to developer of cloud application.
- Software as a Service (SaaS): The SaaS software is hosted by this layer give to the customer by means of Internet. It lessens the maintenance cost and purchase of the customer.
Fig. 2: Cloud computing service
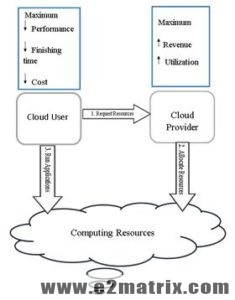
Fig. 3: Cloud usage scenario
Public Cloud: Public cloud or external cloud portrays cloud computing in the customary mainstream. Public clouds are controlled by third parties, and applications from various clients are likely to be together mixed on the networks, storage systems and servers of cloud. A public cloud gives administrations to multiple customers.
Hybrid Cloud: Hybrid clouds consolidate both cloud models of private and public. This is seen frequently with the utilization of storage clouds for supporting Web 2.0 applications.
Private Cloud: Private Clouds are developed for the exclusive utilization of one customer, offering the most extreme control over quality of service, security and data. The company claims the infrastructure and has control over how applications are deployed on it. Private clouds can be developed and oversaw by a cloud provider or by IT organization of a company.
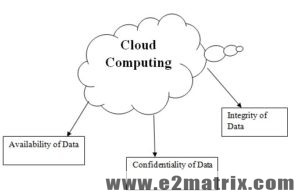
- Confidentiality: It guarantees that least difficult confirmed party can utilize the articles. The endorsed occasions have the predefined ID to section the items. For eg: access to learn, section to see, passage to change and so on. This strategy is named as private or mystery. There is the section oversee ways to deal with help and keep up the privacy like cryptography and encryption.
- Integrity: It insurances that handiest authorized individuals can manage the articles in acknowledged methodologies. Erasing, composing, adjusting notoriety, creating and modifying notoriety are a few changes assortments.
- Availability: It ensures that handiest the endorsed social occasions can use the articles at reasonable conditions. The checked customer first requests to section the thing then approval is given and it can’t be rejected. Accessibility is here and there known as DoS.
Figure 4: Features of Cloud Computing
Cloud computing thesis Implementation
Cloud computing thesis implementation can include various domains:
- Cloud data security
- Job scheduling
- Load Balancing
- Energy aware scheduling
- Workflow scheduling
- Fog Computing
- Green Cloud Computing
- Cloud reports and many more.
Security objectives for Cloud Computing Thesis List
Cloud computing thesis list in terms of security can cover the following objectives
- Protect postal carrier records from unauthorized access, monitoring, disclosure and amendment.
- Protect information sources from deliver chain threats.
- Prevent unauthorized access to cloud computing infrastructure resources.
- Design Web applications deployed in a cloud for an Internet chance model [such as the National Institute of Standards and Technology (NIST)] and embed safety into the software improvement method.
- Protect Internet browsers from attacks to mitigate stop-person security vulnerabilities
- Deploy get entry to manipulate and intrusion-detection technology on the CP and conduct an unbiased assessment to confirm that they’re in vicinity.
Cloud Computing Research Guidance Top threats to cloud computing security
According to Cloud Security Alliance (CSA) the subsequent are the top threats to cloud computing safety. Cloud computing thesis implementation can include the following attacks:
- Data breaches
- Data loss
- Denial of service ranks
- Account or Service traffic hijacking
- Insecure interfaces
- Shared technology vulnerabilities
- Insufficient due diligence
E2matrix is the best approach to complete your cloud computing thesis topics and provides you cloud computing research Guidance from beginning selection included selection of paper, synopsis, coding part with documentation. Our Cloud Computing thesis consultant provides you full guidance with proper readymade cloud computing thesis. For more you can talk to our experts over a phone call at +91-90412-62727 or email at support@e2matrix.com