Mobile Computing vs Green Computing
Computing means any goal-oriented activity requiring, benefiting from, or creating computers. Thus, computing includes designing and building hardware and software systems for a wide range of purposes; processing, structuring, and managing various kinds of information; doing scientific studies using computers; making computer systems behave intelligently; creating and using communications and entertainment media; finding and gathering information relevant to any particular purpose.
GREEN COMPUTING
Green computing is the environmentally responsible and eco-friendly use of computers and their resources. In broader terms, it is also defined as the study of designing, manufacturing/engineering, using and disposing of computing devices in a way that reduces their environmental impact. Many IT manufacturers and vendors are continuously investing in designing energy efficient computing devices, reducing the use of dangerous materials and encouraging the recyclability of digital devices and paper. Green computing is also known as green information technology (green IT). Green computing, or green IT, aims to attain economic viability and improve the way computing devices are used. Green IT practices include the development of environmentally sustainable production practices, energy efficient computers and improved disposal and recycling procedures.
MOBILE COMPUTING
Mobile computing is human–computer interaction by which a computer is expected to be transported during normal usage. Mobile computing involves mobile communication, mobile hardware, and mobile software. Communication issues include ad-hoc and infrastructure networks as well as communication properties, protocols, data formats and concrete technologies. Hardware includes mobile devices or device components. Mobile software deals with the characteristics and requirements of mobile applications. Thus, mobile computing is the ability to use computing capability without a pre-defined location and/or connection to a network to publish and/or subscribe to information The purpose of this paper is to explore the comparison between Green cloud computing and Mobile Cloud computing and security issues and define which common security solutions are.
GREEN CLOUD COMPUTING
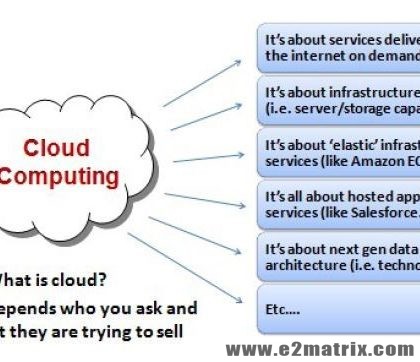
Green cloud is a buzzword that refers to the potential environmental benefits that information technology (IT) services delivered over the Internet can offer society. The term combines the words green — meaning environmentally friendly — and cloud, the traditional symbol for the Internet and the shortened name for a type of service delivery model known as cloud computing.
Benefits of Green Cloud Computing
- Reduced Cost
- Automatic Updates
- Green Benefits of Cloud computing
- Remote Access
- Disaster Relief
- Self-service provisioning
- Scalability
- Reliability and fault-tolerance
- Ease of Use
- Skills and Proficiency
- Response Time
- Increased Storage
- Mobility
Security Issues in Green cloud computing
The chief concern in cloud environments is to provide security around multi-tenancy and isolation, giving customers more comfort besides “trust us” idea of clouds. There has been survey works reported that classifies security threats in cloud based on the nature of the service delivery models of a cloud computing system However, security requires a holistic approach. Service delivery model is one of many aspects that need to be considered for a comprehensive survey on cloud security. Security at different levels such as Network level, Host level and Application level is necessary to keep the cloud up and running continuously. In accordance with these different levels, various types of security breaches may occur.
There are four types of issues raise while discussing security of a cloud.
- Data Issues
- Privacy issues
- Infected Application
- Security issues
Solution to security issues in Green Cloud Computing
1) Control the consumer access devices: Be sure the consumer’s access devices or points such as Personal Computers, virtual terminals, gazettes, pamphlets and mobile phones are secure enough. The loss of an endpoint access device or access to the device by an unauthorized user can cancel even the best security protocols in the cloud. Be sure the user computing devices are managed properly and secured from malware functioning and supporting advanced authentication features.
2) Monitor the Data Access: Cloud service providers have to assure about whom, when and what data is being accessed for what purpose. For example many website or server had a security complaint regarding snooping activities by many people such as listening to voice calls, reading emails and personal data etc.
3) Share demanded records and Verify the data deletion: If the user or consumer needs to report its compliance, then the cloud service provider will share diagrams or any other information or provide audit records to the consumer or user. Also verify the proper deletion of data from shared or reused Many providers do not provide for the proper degaussing of data from drives each time the drive space is abandoned. Insist on a secure deletion process and have that process written into the contract.
4) Security checks events: Ensure that the cloud service provider gives enough details about fulfillment of promises, break remediation and reporting contingency. These security events will describe responsibility, promises and actions of the cloud computing service provider
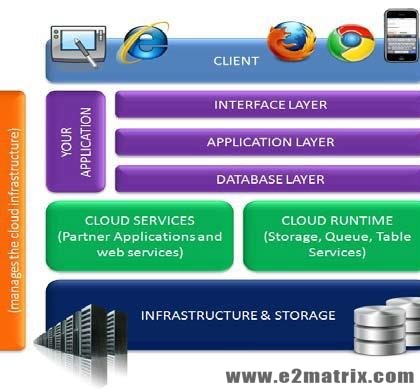
MOBILE CLOUD COMPUTING
Mobile cloud computing is the combination of cloud computing and mobile networks to bring benefits for mobile users, network operators, as well as cloud providers. Cloud computing exists when tasks and data are kept on the Internet rather than on individual devices, providing on-demand access. Mobile apps may use the cloud for both app development as well as hosting. A number of unique characteristics of hosted apps make the mobile cloud different from regular cloud computing. Mobile apps may be more reliant upon the cloud to provide much of the computing, storage, and communication fault tolerance than regular cloud computing does.
Benefits of Mobile Cloud Computing
- Extending battery lifetime
- Improving data storage capacity and processing power
- Improving reliability
Security Issues in Mobile cloud Computing
Cloud computing as opposed to standard computing has several issues which can cause reluctance or fear in the user base. Some of these issues include concerns about privacy and data ownership and security. Some of these concerns are especially relevant to mobile devices. In this section, the paper discusses some of these issues, including both incidents involving them and techniques used to combat them.
- Privacy
- Data Ownership
- Data Access and Security
Solution to Security issues in Mobile Cloud computing
Individuals and enterprises take advantage of the benefits for storing large amount of data or applications on a cloud. However, issues in terms of their integrity, authentication, and digital rights must be taken care of
1) Integrity: Every mobile cloud user must ensure the integrity of their information stored on the cloud. Every access they make must me authenticated and verified. Different approaches in preserving integrity for one’s information that is stored on the cloud is being proposed.
2) Authentication: Different authentication mechanisms have been presented and proposed using cloud computing to secure the data access suitable for mobile environments. Some uses the open standards and even supports the integration of various authentication methods. For example, the use of access or log-in IDs, passwords or PINS, authentication requests, etc.
3) Digital rights management: Illegal distribution and piracy of digital contents such as video, image, audio and e-book, programs becomes more and more popular. Some solutions to protect these contents from illegal access are implemented such as provision of encryption and decryption keys to access these contents. A coding or decoding must be done before any mobile user can have access to such digital contents